6 Steps to Secure Your Industrial Control System
by Julie Gruenholz on Mar 28, 2019 10:30:00 AM

Digital security is a big deal these days. Your whole plant is run by computers. Computers break, software gets corrupted and voila, your whole plant is down and you’re hemorrhaging cash.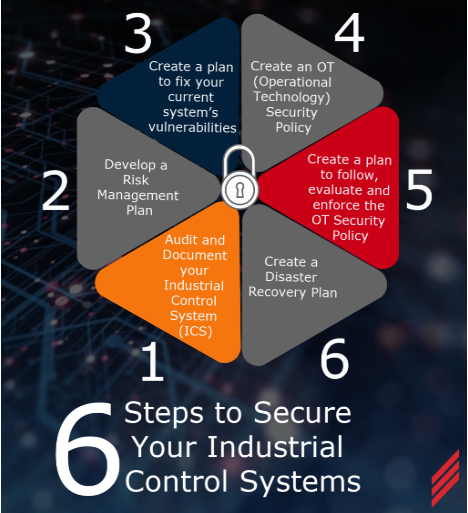 There are enough news stories of foreign governments hacking into our infrastructure to spread fear and get the federal government (DHS/FEMA) and ISA (International Society of Automation) involved. It seems like everyone is writing standards and trying to push security practices into both public infrastructure and private industry. You may think this is a bit of an overreaction. You may not be interested in following international standards or following potential new DHS laws (how could they possibly enforce this – right?) But, you may not have considered that the same consequences can arrive from operator error, hardware failure or internal sabotage.
There are enough news stories of foreign governments hacking into our infrastructure to spread fear and get the federal government (DHS/FEMA) and ISA (International Society of Automation) involved. It seems like everyone is writing standards and trying to push security practices into both public infrastructure and private industry. You may think this is a bit of an overreaction. You may not be interested in following international standards or following potential new DHS laws (how could they possibly enforce this – right?) But, you may not have considered that the same consequences can arrive from operator error, hardware failure or internal sabotage.
Regardless of your concerns, it is a smart business decision to make sure all the equipment that runs your facility is protected. Implementing system cybersecurity is like having an insurance policy on your plant control system. I am a CSSA (Certified SCADA Security Architect) and I recommend the following 6 steps:
Step 1: Audit and Document your Industrial Control System (ICS)
You can’t protect anything unless you know what you have. Facilities evolve over time and the control system architecture gets complicated. You need to audit and document your ICS:
- Network Architecture
- How is everything connected?
- What protocols are used?
- Where are all the components? Who has physical access?
- Which isolated systems rely on product from other isolated systems to work?
- Servers/HMIs/SCADAs/Historians/Batch Controllers:
- How many computers do you have?
- Where are they? Who has physical access?
- What OS are they running? How is security set up?
- What kinds of software is running? How is security set up?
- Is there a connection to the outside world? How is this set up?
- SIS (Safety Instrumented System):
- Do you have one of these?
- How does it integrate into the rest of your Industrial Control System?
- Controllers
- What kinds of controllers do you use?
- How are they digitally accessed?
- Who has physical access?
- Smart Sensors and Smart Actuators
- What kinds of sensors and actuators do you use?
- How are they digitally accessed?
- Who has physical access?
Step 2: Develop a Risk Management Plan
Now that you have your plant documented, you can develop a Risk Management Plan. You need to create an actual document that everyone can agree to and follow. This document will answer the following questions:
- Identification
- How many ways could your system fail?
- Which processes would be compromised?
- Responsibility
- Who cares if something fails?
- Who oversees making sure there are minimal failures?
- Who is responsible for recovering from failure?
- Who is responsible for specifying and installing new equipment?
- Who makes sure the Risk Management Plan is followed?
- Assessment
- What is the fallout if any part of your ICS goes down?
- Which areas of the plant are most important to producing product?
- Which areas of the plant are most vulnerable?
- How long can each component be failed without a serious adverse effect?
- How devastating will it be if a component fails?
- What are the criteria for evaluating the quantitative and qualitative risks?
- Mitigation
- Which risks, and failures, are minor enough that they are irrelevant and can be ignored?
- Which risks, and failures, are acceptable and already have infrastructure and plans in place for recovery?
- Which risks, and failures, need to be planned for and fixed?
- Tracking
- How often is your system audit updated?
- How are your system vulnerabilities continually evaluated?
- How is the Risk Management Plan updated?
- Budget
- Who pays for all this?
- What are the spending priorities?
Step 3: Create a plan to fix your current system’s vulnerabilities
After digesting the Risk Management Plan, you can then move on to plugging the holes and minimizing vulnerabilities in your industrial control system. This will likely include hardware, software and operating procedure modifications.
- How can you tweak your current installation to make it more secure?
- How can you conform with industry best practices?
- What kinds of skills and equipment do you need to accomplish this?
- Will the upgraded systems conform to your new Security Policy (below)?
Step 4: Create an OT (Operational Technology) Security Policy
While simultaneously fixing your system’s vulnerabilities, you need to create a Security Policy. Your IT group might already have a policy in place. It would be a good idea to keep the same vision as them. You should both have the same security goals. Of course, the IT Security Policy will need to be changed considerably to apply the same ideals to your industrial equipment.
- How can you incorporate your company’s values, and the risks outlined in the Rick Management Plan, into your OT Security Policy?
- How can you minimize liability in future design and installation?
Step 5: Create a plan to follow, evaluate and enforce the OT Security Policy
A Security Policy does no good if it doesn’t have legs. You need to lay out a plan to follow, evaluate and enforce all the best practices which need to be put in place. Operations and management need to work together on this. Keep in mind:
- Supporting an OT Security Policy benefits operations by improved in equipment uptime and availability.
- Supporting an OT Security Policy benefits management by reducing the risk of losing money, like having an insurance policy.
Step 6: Create a Disaster Recovery Plan
No system is bullet-proof. You need to minimize risk but be prepared for catastrophe. With all the information that you’ve gathered above, you can get a list of each vulnerable component in your system. Each component that can fail needs a plan put in place as to how you will recover from a failure. The plan needs to include:
- Equipment recovery priorities
- Staff that is responsible for each phase of the recovery
- Staff that is available if a key player is unavailable
- Spare parts / availability of replacement parts from vendors
- Backed-up software location and availability
- And of course, detailed procedures to get everything back up and running.
About the Author
Julie has left Hallam-ICS to pursue other endeavors, but her contributions to the company continue to be valued.
About Hallam-ICS
Hallam-ICS is an engineering and automation company that designs MEP systems for facilities and plants, engineers control and automation solutions, and ensures safety and regulatory compliance through arc flash studies, commissioning, and validation. Our offices are located in Massachusetts, Connecticut, New York, Vermont and North Carolina and our projects take us world-wide.
You May Also Like
These Related Stories

What's new in SQL Server Reporting Services 2016?

Understanding SQL Server Database Backups and Recovery Models





No Comments Yet
Let us know what you think